The "God Mode" API Key Must Die: A Blueprint for Ephemeral Agent Security
Why we need to stop treating AI Agents like service accounts, and how the "Ephemeral Agent Credentialing" pattern fixes it.
We are building AI agents that can code, deploy infrastructure, and query production databases. Yet, in many architectures I see, these autonomous agents are still holding the digital equivalent of a Master Key: a static, long-lived API token hardcoded into an environment variable.
If that agent gets prompt-injected or hijacked, the attacker doesn’t just get the agent they get the key. And if that key is valid for a year, you have a massive problem.
We need a better standard for agentic security.
I’ve been working on a solution for this in the AI Security Blueprints repository, and today I’m releasing Version 1.1 of the Ephemeral Agent Credentialing pattern.
🛑 The Problem: Static Trust in a Dynamic World
Traditional service accounts assume a static identity. But AI agents are:
Ephemeral: They spin up, do a job, and vanish.
Unpredictable: They might need access to S3 one minute and GitHub the next.
Vulnerable: They process untrusted user input (prompts) directly.
Giving a permanent credential to an entity that parses untrusted input is a security anti-pattern.
🛠 The Solution: Ephemeral Agent Credentialing
This pattern proposes a shift from “Stored Trust” to “Just-in-Time Trust.”
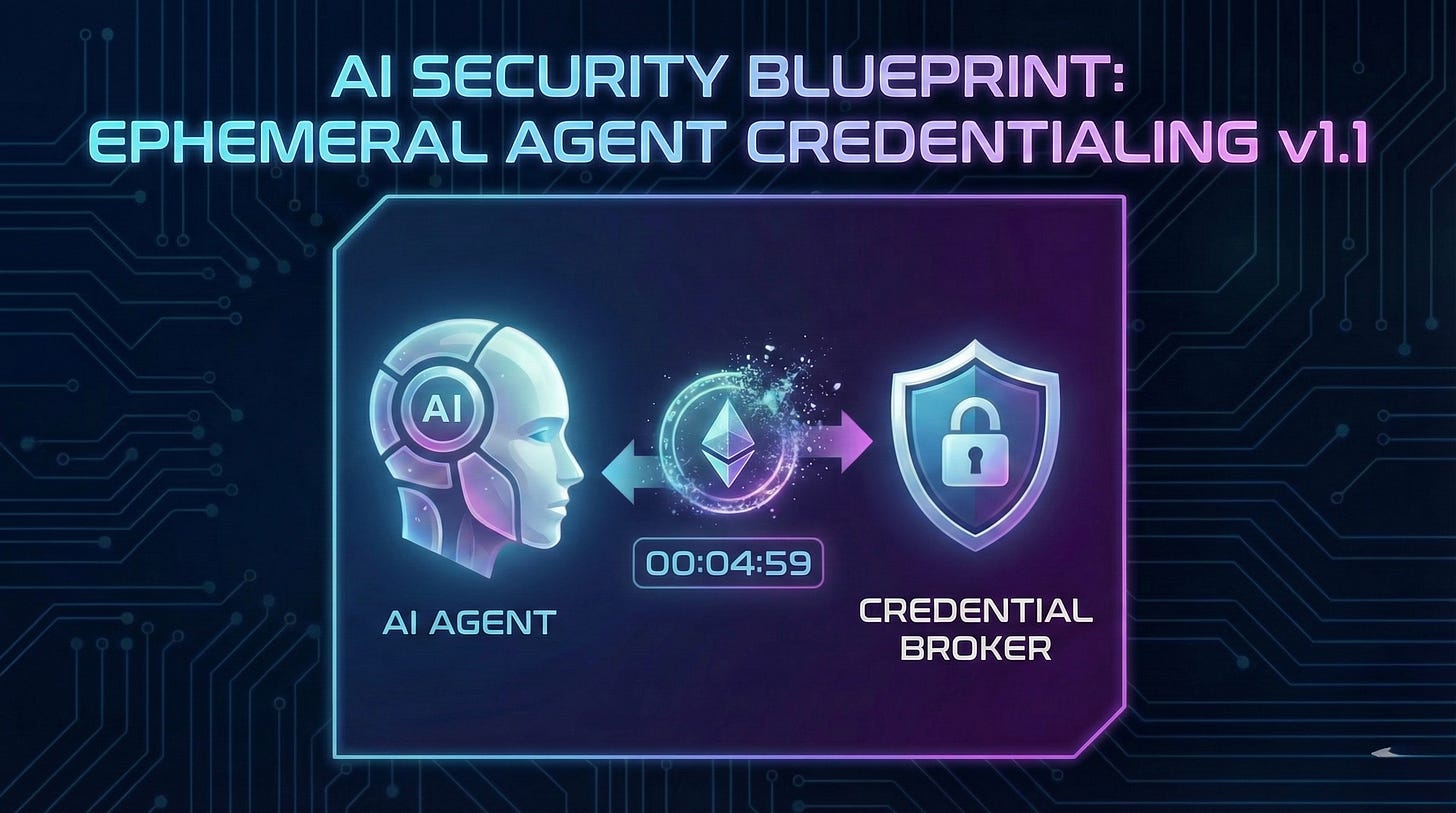
Instead of giving the agent a key, we give the agent a way to prove who it is. The agent then exchanges that proof for a short-lived, scope-down token valid only for the specific task at hand.
The Flow at a High Level:
Boot & Attest: The agent initializes. Instead of loading secrets, it loads a cryptographic identity (like a SPIFFE ID or an OIDC token from its cloud host).
Exchange: When the agent needs to call a tool (e.g., “Search Customer Database”), it sends its identity + the request to a Credential Broker.
Mint: The Broker verifies the identity and mints a token valid for exactly 5 minutes (or the duration of the task) with permissions scoped only to that specific database.
Destruct: Once the task is done, the token expires. If the agent is hijacked 10 minutes later, the attacker finds nothing but expired junk.
🔄 What’s New in v1.1 ?
I’ve just pushed the v1.1 update to the blueprint, which refines the architecture based on early feedback.
Refined Threat Model: We dig deeper into what happens if the Broker is compromised vs. the Agent.
Granular Scoping: Updated definitions on how to scope tokens to individual tools rather than whole APIs.
Auditability: A heavy focus on how to trace actions back to the specific session ID of the agent, not just its generic role.
🧪 I Need Your Eyes on This
Security patterns only survive if they are battle-tested. I am not releasing this as a “finished product,” but as a Request for Comments (RFC).
I need security engineers, AI architects, and DevOps builders to look at this spec and tell me:
Where does this break in your stack?
Is the complexity of a Credential Broker worth the security gain for your use case?
How do we handle the latency of token minting in real-time agent conversations?
Read the Full Pattern (v1.1) on GitHub
Let’s build the security standards for the Agentic Age before the incidents force us to.